Mobile devices, often filled with personal data, have seen significant improvements in security over the years. However, companies like Cellebrite provide law enforcement with tools capable of circumventing the safeguards on certain models. While Cellebrite typically maintains a level of secrecy regarding its technologies, an anonymous source recently shared insights after attending a Cellebrite briefing, exposing vulnerabilities in Google’s Pixel phone lineup.
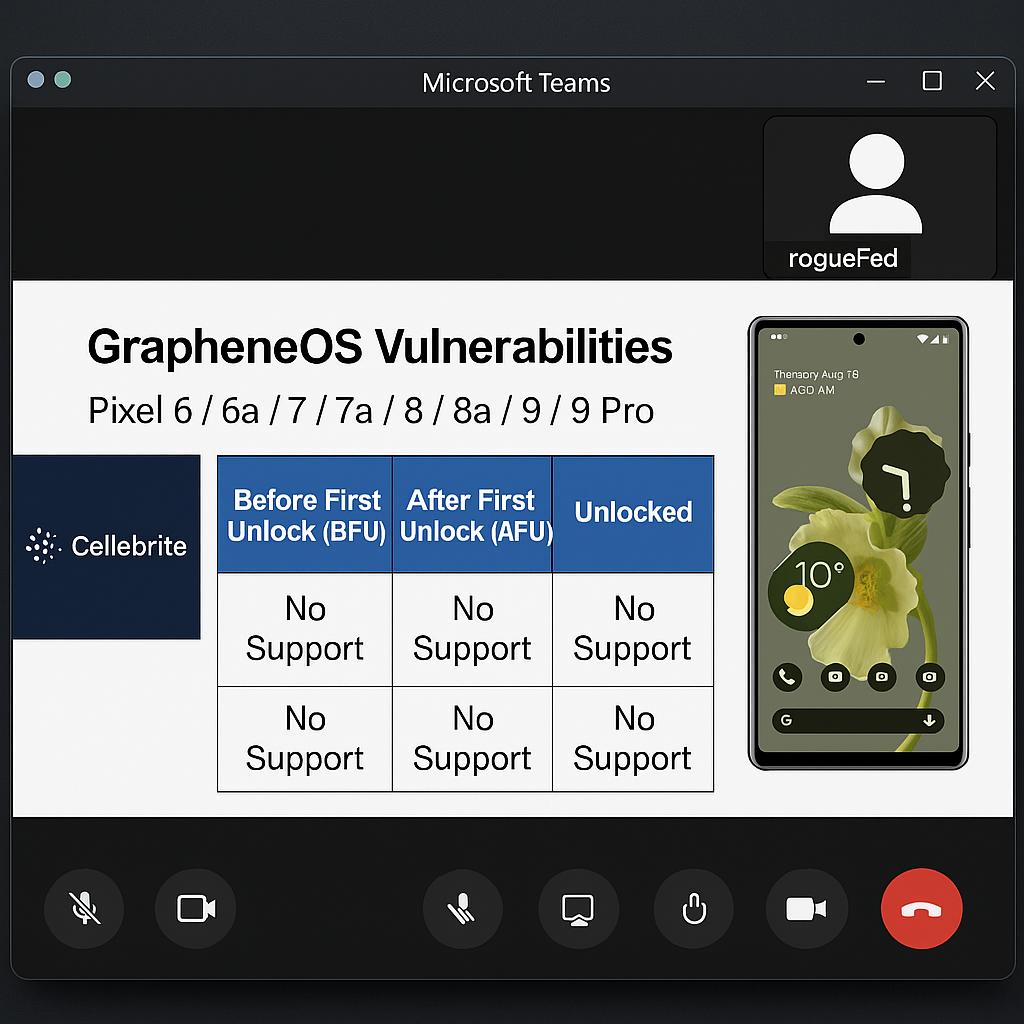
The individual, known by the moniker rogueFed, shared screenshots from a Microsoft Teams meeting on GrapheneOS forums, as reported by 404 Media. GrapheneOS is an Android-based operating system designed to enhance security and is compatible with select Pixel models, eliminating reliance on Google services. Its rising popularity among security advocates seems to have prompted Cellebrite to assess this platform’s vulnerability.
The leaked information highlights the Pixel 6, 7, 8, and 9 series, but notably omits the recently launched Pixel 10. Cellebrite’s findings categorize phone support into three conditions: before first unlock (BFU), after first unlock (AFU), and unlocked. The BFU state, where the phone has not been accessed since a restart, retains maximum encryption, offering significant security. Conversely, the AFU state allows for easier data extraction, while an unlocked phone poses the greatest risk for data compromise.
According to Cellebrite, the GrapheneOS platform presents greater security than the standard Google Android configuration. In its briefings, Cellebrite asserted that its technology could extract data from the Pixel 6, 7, 8, and 9 in all three states on stock software. However, it cannot bypass passcodes for full device control nor can it replicate an eSIM from Pixel devices, which is relevant as the Pixel 10 series transitions away from physical SIM cards.
On devices running GrapheneOS, law enforcement faces significant challenges, as the Cellebrite documentation indicates that access is only possible with software versions prior to late 2022—after which the Pixel 8 and 9 were launched. Phones that are up to date in both BFU and AFU states offer protection against data extraction from Cellebrite, and by late 2024, even fully unlocked GrapheneOS devices will be insulated from data copying. While an unlocked phone can be examined through various methods, data extraction is constrained to the information accessible to the user.
Also Read : Commanders Struggle Against Chiefs in 28-7 Loss: A Diminished Season Continues
The original leaker noted they participated in two sessions undetected but also criticized the meeting facilitator by name. As a result, it is likely that Cellebrite will enhance security measures for future meetings.
We have reached out to Google to understand why a community-created custom ROM demonstrates higher resistance to phone hacking tools compared to its official operating system. Updates will be provided should Google respond.